SHA256 Hash Generator Online Tool
About SHA256 Hash Generator Online Tool:
This online SHA256 Hash Generator tool helps you to encrypt one input string into a fixed 256 bits SHA256 String.
Paste your Input String or drag text file in the first textbox, then press "SHA256 Encrypt" button, and the result will be displayed in the second textbox.
SHA256 and Blockchain Security:
SHA-256 is designed by NSA, it's currently most used Hash algorithm. SHA-256 is used in two parts of the Blockchain network: generate new bitcoin address and the "proof of work" algorithm used in mining.
This is to prove a proof of workload (power consumption), making it difficult to find a proof, to consume a lot of computing resources, but verifying its should be easy.
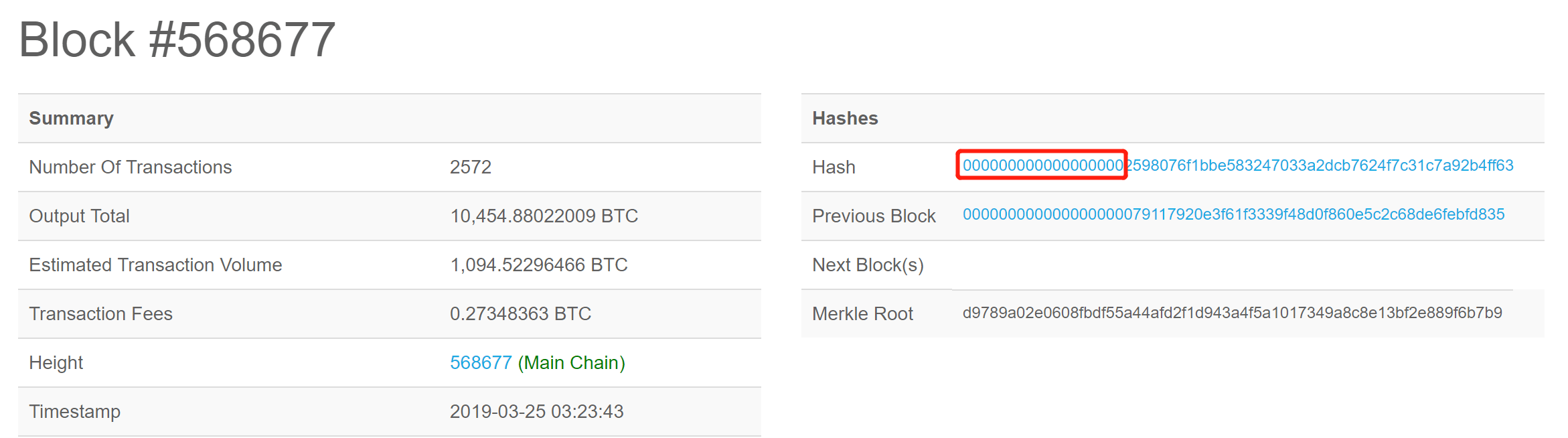
For Bitcoin mining, the sign of successful mining is to find a string of numbers x such that the first n (binary) bits of f(x) are zero. In principle, f(x) must be irreversible, and the output is uniform. Generally, this function is called a hash function. Sha256 was chosen because it is a well-recognized hash function recognized at this stage. It is okay to choose MD5 for more than ten years. I think that after a dozen years, maybe sha256 will become unsafe.
For a safe hash function, it is known that the first n bits of f(x) are 0. The best way to find x is to try-error, that is, randomly generate x to calculate f(x) until the result meets the requirements. This success rate is 1/(2^n), and the cost of successful mining increases with the n-index. Others who see the string you find meet the requirements, you can know that you have tried 2^n other strings to find this string, which can be used as a proof of the workload, thus recognizing your string and participating in the transaction in the future.
Does SHA256 Hash Generator Online Tool log my data?
Absolutely NOT, this SHA256 Hash Generator doing all the formatting work on the client side, all logic are implemented by Javascript. There are 2 major advantages: 1.Your data never transmitted in the Open Internet, so you know it's secure; 2.It's much faster than doing all the work in the server side, because there is no Internet Delay.
More information about SHA256:
RFC 3174: https://tools.ietf.org/html/rfc3174
Python Implementation of SHA256 (hashlib): https://docs.python.org/3/library/hashlib.html
Java Implementation of SHA256: https://docs.oracle.com/javase/7/docs/api/java/security/MessageDigest.html
PHP Implementation of SHA256: http://php.net/manual/en/function.hash.php
SHA256 Generator with Python (with package hashlib):
import hashlib
def sha256_generator(str):
m = hashlib.sha256()
m.update(str.encode())
return m.hexdigest()
SHA256 Generator with Java (with package MessageDigest):
import java.math.BigInteger;
import java.security.MessageDigest;
public String generate(String str){
MessageDigest md = MessageDigest.getInstance("SHA-256");
md.update(str.getBytes());
byte[] digest = md.digest();
String result = new BigInteger(1, digest).toString(16).toUpperCase();
return result;
}
SHA256 Generator with Linux (with OpenSSL):
root@instance-1:/var/log/apache2# openssl dgst -sha256 access.log
SHA256(access.log)= 1c830df491ff2e9dc4043ac9e89a2380cbb621d80331bbddd0cbcb4f6e502cf8